Here’s what you need to know about Web server DDoS attacks, how to defend against them and what tools are available to help in your efforts.
- Source: Defending Against Apache Web Server DDoS Attacks
- Also See: http://tltech.com/info/rewriterule-in-htaccess-vs-httpd-conf/
- Also See: https://wordpress.org/support/topic/wp-admin-locked-down-through-htaccess-but-still-getting-tons-of-login-attempts
- Also See: https://www.digitalocean.com/community/tutorials/how-to-set-up-mod_security-with-apache-on-debian-ubuntu
- https://blog.vigilcode.com/2011/05/ufw-with-fail2ban-quick-secure-setup-part-ii/
- http://xplus3.net/2013/05/09/securing-xmlrpc-wordpress/ – scripts to add for xmlrpc hack
- https://rbgeek.wordpress.com/2014/09/11/block-wordpress-xmlprc-php-ddos-attacks-using-fail2ban/
- http://linuxaria.com/howto/how-to-protect-apache-with-fail2ban additional advice to monitor apache log for script searches
About Fail2ban
The third method for protecting your Web server is Fail2ban. Fail2ban scans log files and bans IPs that show malicious signs. It is most often used to block SSH knock attempts, but you can also use it to block repeated requests to your Web resources.
Fail2ban uses a list of regular expressions and checks these expressions against a set of log files. If there are matches that go beyond a certain threshold, then the source IP of the request is blocked. The IP is blocked on a network level.
Similar to mod_evasive, the installation on Ubuntu is easy.
sudo apt-get install fail2ban
After installing the package, you have to copy the default configuration file to a working configuration file.
sudo cp /etc/fail2ban/jail.conf /etc/fail2ban/jail.local
Add your own management and proxy networks to ignoreip and set a proper destemail email address for block notifications. I also advise you to set usedns to no.
Fail2ban uses jails to describe services that have to be protected. By default, Fail2ban enables the SSH jail. If you don’t want this, then disable the SSH jail. You can then add this apache-ddos jail to hold the custom configuration settings for protecting your Web server. Note that you can use pattern matching in the logpath (e.g., /var/log/apache*/*access.log).
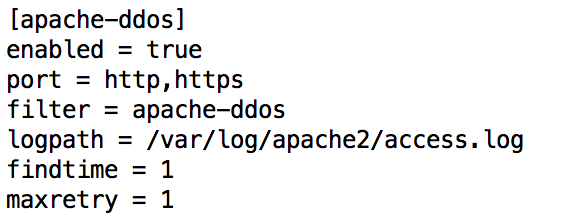
This will start a jail with the filter apache-ddos. The filters are defined in /etc/fail2ban/filter.d/. Add the file apache-ddos.conf to this location.
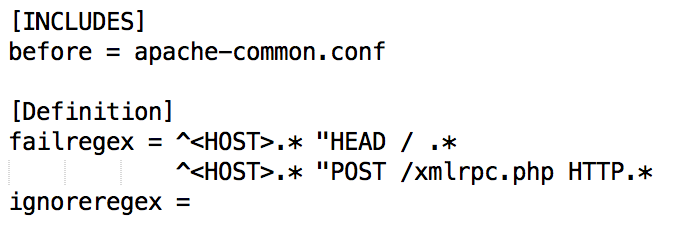
The above code will block IPs that do repeated request for HEAD or IPs that do repeated POST requests to xmlrpc.php. If you are not sure about the exact configuration or regular expressions, then have a look at the provided examples (e.g., apache-badbots, apache-noscript, etc).
The list of blocked IPs can be viewed if you list the active firewall rules (iptables -L -n). You can remove a blocked IP with:
fail2ban-client set apache-ddos unbanip 1.2.3.4
The fail2ban-client command is a useful command-line utility to get the status of the current jails, reload configuration, add individual IPs to the jail or stop and restart the service.
